Cisco Duo Anyconnect
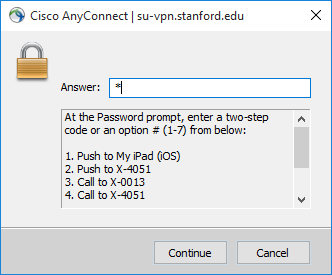
Depending on how your company configured Duo authentication, you may or may not see a “Passcode” field when using the Cisco AnyConnect client.
Single Password with Automatic Push
Install and Run Cisco's AnyConnect client for VPN connectivity on Windows including Duo This article refers to the Cisco AnyConnect VPN. If you're looking for information on the Prisma Access VPN Beta that uses the GobalConnect app, see: Prisma Access VPN Beta Landing Page. Mar 06, 2020 Cisco ASA SSL VPN for Browser and AnyConnect Duo integrates with your Cisco ASA VPN to add two-factor authentication to any VPN login. VPN: Using Duo Append Mode with Cisco AnyConnect Certain Departmental Pools, Full Tunnel VPN, and Split Tunnel VPN Pools require Two-Factor Authentication (2FA) through Duo Security to connect. Since the Cisco AnyConnect application does not allow you to choose your authentication method using Duo Prompt, you can use the Duo Append Mode.
If AnyConnect only prompts for a password, like so:
After you submit your login information, an authentication request is automatically sent to you via push to the Duo Mobile app or as a phone call.
Alternatively, you can add a comma (“,”) to the end of your password, followed by a Duo passcode or the name of a Duo factor. Here's how:
| Type... | To... |
|---|---|
| password,passcode | Log in using a passcode, either generated with Duo Mobile, sent via SMS, generated by your hardware token, or provided by an administrator. Examples: 'mypass123,123456' or 'mypass123,1456789' |
| password,push | Push a login request to your phone (if you have Duo Mobile installed and activated on your iOS, Android, or Windows Phone device). Just review the request and tap 'Approve' to log in. |
| password,phone | Authenticate via phone callback. |
| password,sms | Get a new batch of SMS passcodes. Your login attempt will fail — log in again with one of your new passcodes. |
You can also add a number to the end of these factor names if you have more than one device registered. For example, push2 will send a login request to your second phone, phone3 will call your third phone, etc.
Examples
To use Duo Push if your password is 'hunter2', type:
To use the passcode '123456' if your password is 'hunter2', type:
To send new SMS passcodes to your second phone if your password is 'hunter2', type:
The comma is Duo's default separator character between your password and the Duo factor. Your administrator may have changed this to a different character. Be sure to follow the instructions sent to you by your organization if they differ from what's shown here.
Second Password for Factor Selection
If AnyConnect shows a 'Second Password' input field (note that your AnyConnect administrator may have changed the 'Second Password' label to something else):
Use the 'Second Password' field to tell Duo how you want to authenticate. Here's how:
| Type... | To... |
|---|---|
| A passcode | Log in using a passcode, either generated with Duo Mobile, sent via SMS, generated by your hardware token, or provided by an administrator. Examples: '123456' or '1456789' |
| push | Push a login request to your phone (if you have Duo Mobile installed and activated on your iOS, Android, or Windows Phone device). Just review the request and tap 'Approve' to log in. |
| phone | Authenticate via phone callback. |
| sms | Get a new batch of SMS passcodes. Your login attempt will fail — log in again with one of your new passcodes. |
Cisco Anyconnect Duo App
You can also add a number to the end of these factor names if you have more than one device registered. For example, push2 will send a login request to your second phone, phone3 will call your third phone, etc.
Examples
To send a Duo Push request to your primary phone, type:
To send a Duo Push request to your secondary phone, type:
To use the passcode '123456', type:
To send new SMS passcodes to your second phone, type:
Introduction
This document describes how to configure a Duo Lightweight Directory Access Protocol (LDAP) identity source object through REST API and using this object in the Remote Access VPN (RA VPN) connection profile as a secondary authentication identity source on Firepower Threat Defense (FTD) managed by Firepower Device Manager (FDM).
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Basic knowledge of RA VPN configuration on FDM.
- Basic knowledge of REST API and FDM REST API Explorer.
- Cisco FTD running version 6.5.0 and above managed by Cisco Firepower Device Manager (FDM).
- FTD registered with the smart licensing portal with Export Controlled Features enabled (in order to allow RA VPN configuration tab to be enabled).
- AnyConnect Licenses enabled (APEX, Plus or VPN-Only).
Components Used
The information in this document is based on these software and hardware versions:
- Cisco FTD running version 6.5.0-115
- Cisco AnyConnect Secure Mobility Clientversion 4.7.01076
- Postman or any other API development tool
- Duo web account
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
From FTD version 6.5, you can use Duo LDAP Identity Source object directly in the RA VPN profile for secondary authentication with the help of REST API.
Prior to this version, two-factor authentication was supported only via Duo Proxy and RADIUS.
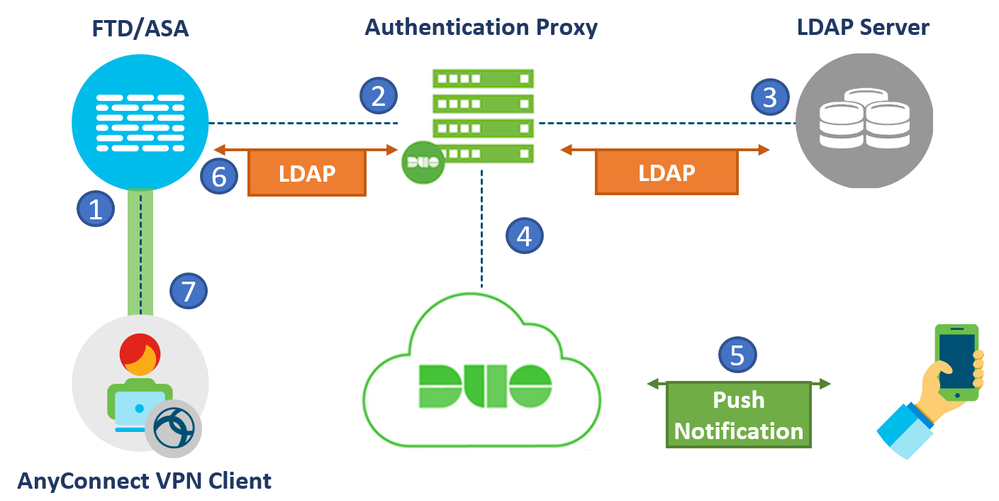
Authentication Flow
Authentication Flow Explained
- The user initiates a remote access VPN connection to the FTD and provides a username and password for Primary Authentication.
- FTD sends the authentication request to the primary authentication server.
- Once the primary authentication is successful, FTD sends a request for secondary authentication to the Duo LDAP server.
- Duo then authenticates the user, depending on the input for secondary authentication (push, passcode, phone).
- Duo responds to the FTD to indicate whether the user authenticated successfully.
- If the secondary authentication was successful, the FTD establishes a remote access VPN connection.
Configure
In order to complete the configuration take into consideration these sections:
Configuration on Duo Administration Portal
Step 1. Login to your Duo account (https://admin.duosecurity.com).
Navigate to Applications > Protect an Application.
Step 2. Select your Authentication Application as Cisco ASA SSL VPN.
Integration Key, Secret Key, and API hostname are used while Duo LDAP object is added through the REST API.
Note: Do not select Cisco Firepower Threat Defense as it is used to add Duo as a Proxy Server.
Step 3. Create a username and activate Duo Mobile on the end device.
Add yourself to the Duo cloud administration webpage. Navigate to Users > Add users
Note: Ensure the end-user has the Duo app installed on.
Step 4. Add your phone number for the automatic generation of code.
Step 5. Select ActivateDuo Mobile.
Step 6. Select Generate Duo Mobile Activation Code.
Step 7. Select Send Instructions by SMS.
Step 8. In order to enroll in the Duo app, click on the link in the SMS. Your account details can be seen in the Device Info section, as shown in the image.
Configuration on POSTMAN
Step 1. Launch the API Explorer of the FTD on a Browser Window.
Navigate to https://<FTD Management IP>/api-explorer
For the configuration displayed the following URL is used: https://10.197.224.99/api-explorer This contains the entire list of API available on the FTD.
It is divided based on the main feature with multiple GET/POST/PUT/DELETE requests which is supported by the FDM.
Note: In this example, we have used POSTMAN as the API.
Step 2. Add a Postman collection for Duo.
Give a name for the collection.
Edit the Authorization tab and update the type to OAuth 2.0
Step 3. Add a new request Auth to create a login POST request to the FTD in order to get the token to authorize any POST/GET requests.
The Body of the POST request must contain these:
| Type | raw - JSON (application/json) |
| grant_type | password |
| username | Admin Username in order to log in to the FTD |
| password | The password associated with the admin user account |
POST Request : https://<FTD Management IP>/api/fdm/latest/fdm/token
The Body of the Response contains the access token which is used in order to send any PUT/GET/POST requests from the FTD.
Step 4. Create Get Interface information request to get the interface details through which Duo would be reachable.
The Authorization tab must contain the following for all subsequent GET/POST requests:
| Type | Bearer Token |
| Token | The access token received by running the login POST Request |
The Body of the Response contains the interface information (version, name, id, type).
Step 5. Add CreateDuoLDAPIdentitySource request to create the Duo LDAP object.

The body of the POST request must contain these:
| Name | Name for Duo LDAP object |
| apiHostname | Duo hostname received from Duo admin portal |
| port | 636 |
| timeout | 60 seconds |
| integrationKey | ikey received from Duo admin portal |
| secretKey | skey received from Duo admin portal |
Note: Timeout is added as 60 seconds for the purpose of this document. Please add the settings as per your network environment.
The URL and sample body for POST request can be copied from the API explorer .
POST Request : https://<FTD Management IP>/api/fdm/latest/object/duoldapidentitysources
The Body of response shows Duo configuration ready to be pushed to the device.
Configure FDM
Step 1. Verify Device is registered to Smart Licensing.
Step 2. Verify AnyConnect licenses are enabled on the device.
Step 3. Verify Export-controlled Features is enabled in the token.
Add Duo Certificate on FDM
You need to download the CA certificate from the Duo website and add it to FDM in-order for LDAP over SSL to work.
Cisco Anyconnect Will Not Connect
Step 1. Login to FDM and then navigate to Objects > Certificates > Add Trusted CA Certificates.
Step 2. Provide a name for certificate object and add the CA certificate downloaded from https://duo.com
Step 3. Deploy the certificate to the device.
Create Local User for Primary Authentication
Step 1. Navigate to Objects > Users and click on + to add a new user., as shown in the image.
Step 2. Add the username and password details and click on OK, as shown in the image.
Note: This document assumes that the RA VPN is already configured. Please refer to the following document for more information on How to configure RA VPN on FTD managed by FDM.
Cisco Anyconnect Duo Yubikey
Binding Duo object to RA VPN on FDM
Step 1. Bind the Duo object as the secondary authentication method in Remote Access VPN.
Navigate to Remote Access VPN and edit the concerned Connection Profile, as shown in the image.
Select LocalIdentitySource as Primary Identity Source and Duo as Secondary Identity Source. Click on Next to close the Remote Access VPN Wizard.
Note: Use Primary username for Secondary login is checked under Advanced option for the purpose of the document. If you need to use different usernames for Primary and Secondary authentication, you can uncheck it.
Step 2. Deploy the configuration to the device.
Pending changes show Local user, Duo object and Secondary Authentication Settings ready to be pushed.
Verify
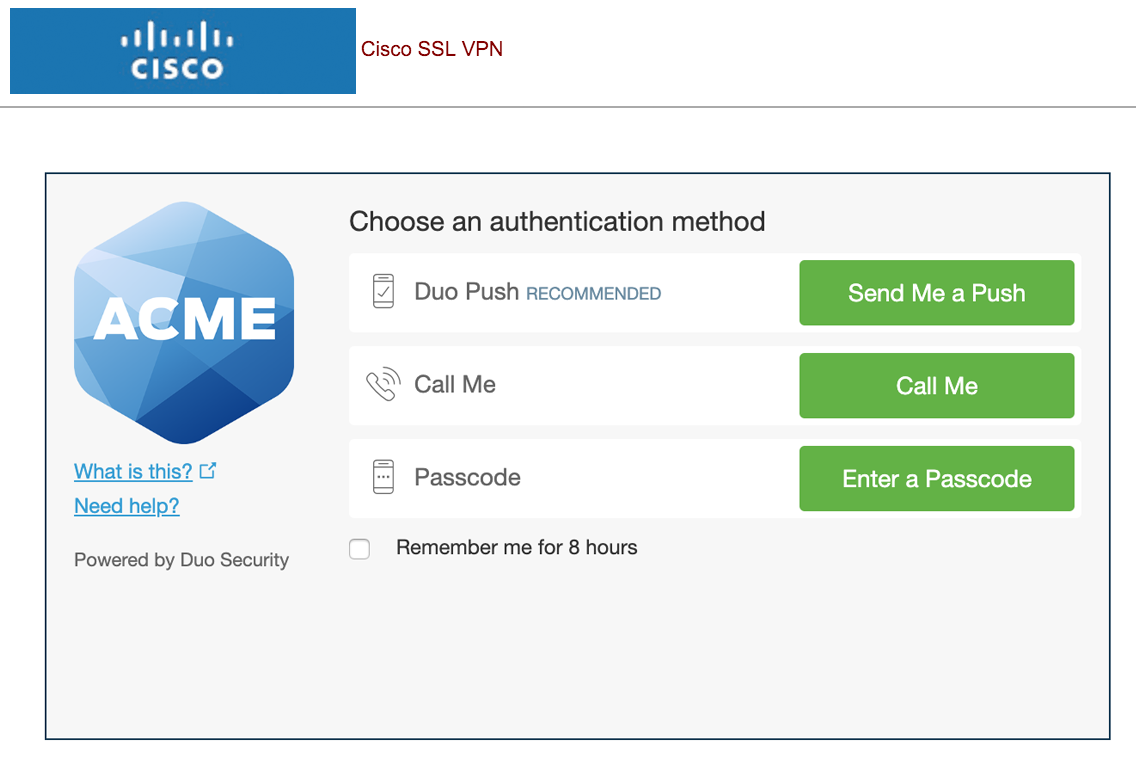
In order to test this configuration, provide the local credentials in Username and Password. For Second Password type push, phone, passcode to determine kind of notification to be sent by Duo. Here push method is used.
Cisco Duo App
You must get a Duo PUSH notification on your enrolled device for Two Factor Authentication (2FA). Once the push request is approved anyconnect user gets connected.
Open Anyconnect GUI >Settings > Statistics and verify the connection.
Verify the user connection on FTD CLI using the show command show vpn-session anyconnect
Troubleshoot
Verify if Duo object is pushed from REST API by navigating to Objects >Identity Sources
Verify the aaa-server configuration and secondary authentication FTD CLI using the show command show run aaa-server <name> and show run tunnel-group
Debug Commands
Note: Refer to Important Information on Debug Commands before you use debug commands.
You can set various debug levels. By default, level 1 is used. If you change the debug level, the verbosity of the debugs might increase. Do this with caution, especially in production environments.
These debugs on the FTD CLI would be helpful in troubleshooting AnyConnect connection for Duo.
